An Operational Assessment of PLA Autonomous Airpower
Deconstructing the Doctrine, CONOPS, and Core Challenges of China's Manned-Unmanned Force
(6/27: I updated the post with additional analysis of MUM-T activities.)
In the first part of this series, I broke down the technical architecture—the datalinks, hardware, and algorithms—that underpins the People’s Liberation Army’s (PLA) autonomous airpower. Now, we shift from engineering to execution and operational art.
To start, two points to frame our analysis.
First, the timeline. The PLA is working to field many of these autonomous systems and maturing/integrating them into the force by 2035—when the PLA is set to “basically complete” its modernization. This analysis, therefore, focuses on the capabilities and concepts the PLA aims to employ within the next ten years or so.
Second, I want to build on existing scholarship. The China Aerospace Studies Institute (CASI) recently published an awesome report, “PLA Concepts of UAV Swarms and Manned/Unmanned Teaming,” which provides a thorough survey of the PLA’s doctrinal literature. Here we’re going to apply a lot of the concepts identified by CASI to a specific, high-escalation scenario: a direct conflict with the United States during a Taiwan contingency.
A Phased, Global War Plan
In a Taiwan conflict, the PLA would prosecute two major campaigns simultaneously: the blockade or invasion itself, and a parallel counter-intervention campaign designed to deter, delay, or defeat U.S. forces. This second campaign would be a proactive, global effort from the outset, informed by PLA concepts like “all-domain joint operations” (全域联合作战) and “systems destruction warfare” (体系破击战). The goal is to create a multi-axis crisis for U.S. decision-makers, attacking the American “operational system” across domains and geography to prevent it from ever effectively intervening in the Taiwan Strait. Autonomous systems are one of the lynchpins of this strategy, providing a range of scalable options from tactical disruption to strategic shock.
Phase 0: Stealthy Posturing (D-90 to D-Day)
The war against the U.S. would begin months before the first shot is fired. In this shaping phase, the PLA would use autonomous and unmanned systems to build a comprehensive intelligence picture and covertly pre-position forces. Long-endurance UCAVs like the WZ-7 Soaring Dragon and WZ-8 supersonic reconnaissance drone would increase their patrol tempo, establishing a baseline of “normal” activity to mask their final wartime positioning while collecting detailed imagery and signals intelligence on key U.S. facilities. This is a direct application of what Chinese writings call “invasive lone wolf warfare” (侵入式独狼作战), whereby an autonomous system conducts deep-penetration ISR or strike operations independently.
More ominously, this is the phase where the PLA’s most asymmetric capabilities would be put in place. For example, “container weapons” (火力盲盒)—a concept involving drone swarms or missiles systems hidden inside commercial shipping containers—would be moved via global logistics networks to commercial ports near critical U.S. military hubs. The operational security challenge for the PLA during this phase would be immense, as any discovery would compromise a key element of its strategic surprise.
Phase 1 & 2: The First Salvo and Coordinated Strikes (D-Day to D+14)
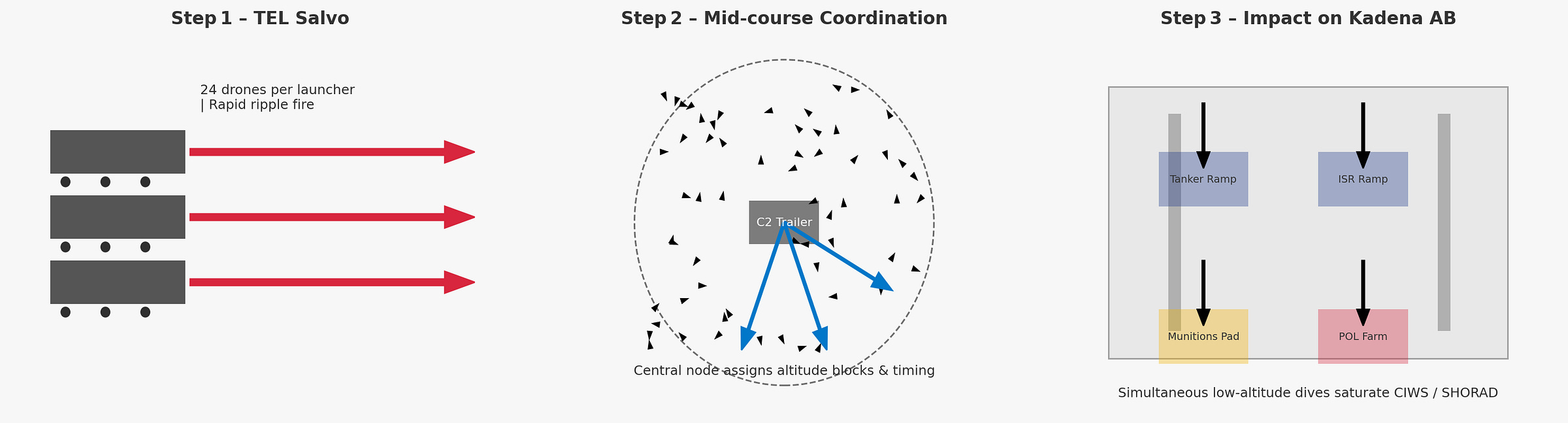
At H-Hour of the Taiwan invasion, the counter-intervention campaign would begin kinetically. The PLA’s initial moves would be designed to achieve operational paralysis, crippling the ability of U.S. forces in the First Island Chain to intervene. The CONOP for this mission is “Bee Swarm Warfare” (蜂群战). This involves saturation attacks by hundreds of land-based, canister-launched drones. These would likely be fixed-wing platforms with simple EO/IR or anti-radiation seekers, fired from mobile Transporter Erector Launchers (TELs). The targets would be selected for operational leverage: the fields of parked KC-135 tankers and RC-135 ISR platforms, exposed munitions assembly areas, and, most critically, the massive, above-ground POL farms at Kadena Air Base.
In parallel with these massed swarm attacks, Manned-Unmanned Teaming (MUM-T) formations would execute more surgical strikes. A twin-seat J-20S, acting as a command node, could direct a stealthy GJ-11 “loyal wingman” (忠诚僚机) to penetrate air defenses and passively geolocate a high-value target like an AN/TPY-2 radar. The J-20S could then launch a long-range weapon from standoff range, neutralizing a key threat without exposing the manned pilot.
The command and control (C2) of such an attack is a non-trivial challenge. The PLA would need to deconflict the flight paths of hundreds of drones and missiles launched from different mobile launchers to ensure they arrive on target in coordinated waves, overwhelming defenses without interfering with each other. This likely requires a centralized ground-based command element, which itself becomes a high-value target for U.S. counter-strikes.
As U.S. carrier strike groups surge towards the theater, the campaign would escalate to directly counter them, employing multiple, layered autonomous concepts.
First, the PLA would use MUM-T formations in an anti-air role to establish air superiority and protect its own forces. With the U.S. CSG pulsing closer, its F/A-18 and F-35C air wing becomes the primary threat to the PLA’s amphibious forces. The J-20’s main mission here is to establish a defensive Combat Air Patrol. In this role, the J-20 acts as the command node for its loyal wingmen, which serve as forward sensors and external weapons arsenals. The unmanned platforms would be sent ahead to detect incoming U.S. aircraft, allowing the J-20 to remain electronically silent and engage with a “first look, first shot” advantage.
Second, and more critically for the PLA’s A2/AD strategy, MUM-T formations would be tasked with the anti-ship ISR mission. To enable a long-range missile strike, the PLA must first find and fix the moving CSG. To solve this, a J-20S or AEW&C aircraft like the KJ-3000 would direct a stealthy UCAV wingman to perform the high-risk penetration of the carrier’s defensive bubble. The drone’s sole purpose is to provide real-time, fire-control-grade targeting data on the carrier back to the PLA Rocket Force, cueing the DF-21D and DF-26 anti-ship ballistic missiles. Here, the drone is a disposable sensor and the J-20 is the C2 link; neither is the primary shooter.
A third, complementary layer would be “Mothership Warfare” (舰群战), focused on saturating defenses. This concept involves platforms like the H-6K bomber and new Jiu Tian SS-UAV launching heterogeneous waves of UCAVs from standoff ranges. These drones, carrying a mix of kinetic warheads, jammers, and decoys, are not intended to sink the carrier themselves. Their objective is magazine depletion: forcing the CSG’s Aegis escorts to expend their finite supply of high-end interceptors on low-cost drones, thereby creating a window of vulnerability for the main missile salvos to strike home.

Phase 3 & 4: Horizontal Escalation and Protracted Operations (D+14 onward)
If the conflict continues, the PLA’s strategy would shift to one of sustained, global pressure, designed to disrupt the flow of U.S. reinforcements and raise the political cost of the war. This is where the PLA’s concept of “Far Seas Defense” (远海防卫) comes into play, aiming to force the U.S. to split its attention across multiple theaters.
Autonomous systems would be critical to interdicting U.S. Sea Lines of Communication (SLOCs). PLA nuclear attack submarines (SSNs), like the Type 095, would be forward-positioned along the key transit routes from San Diego to Guam. These submarines, in a clear naval application of MUM-T, could launch their own UCAVs to the surface to provide over-the-horizon targeting for anti-ship cruise missiles against U.S. logistics vessels and reinforcement convoys. In the Indian Ocean, a PLA Surface Action Group, centered on a Type 055 cruiser and supported by its own organic drones, would threaten the key U.S. base at Diego Garcia, forcing the U.S. to divert naval assets away from the primary fight in the Pacific.
It is in this phase that the PLA might decide to activate its container swarms. A surprise attack on a CONUS-based shipyard or logistics hub would be the ultimate act of horizontal escalation, designed to shatter the U.S. public’s sense of security and force a strategic re-evaluation of intervention. From Beijing’s perspective, such a high-risk mission would be justified by its potential to directly attack the adversary’s political will to continue the fight.

Concluding Thoughts
As we trace the narrative of the PLA’s counter-intervention plan, from the tactical swarms in Phase 1 to the strategic shock of Phase 3, a unifying thread emerges. The PLA employs a multi-layered and ambitious war plan that leverages autonomous systems to create dilemmas for U.S. commanders at every phase of the conflict. However, core challenges for the PLA are geographic and architectural as well as technological. Its most potent counter-intervention concepts, such as “Mothership Warfare,” require projecting power thousands of miles from the Chinese mainland. This creates an immense dependency on what is perhaps its most critical vulnerability: long-haul command, control, and communications.
A UCAV launched from a Jiu Tian mothership over the Philippine Sea is operationally inert if it cannot receive updated commands or transmit its sensor data back to a shooter. The architecture hinges on reliable, high-bandwidth satellite communications. These SATCOM links are fragile, creating a clear and targetable vulnerability for U.S. Space Force offensive electronic warfare and potential counter-space operations. (I plan on examining China’s growing SATCOM capabilities in a future article).
Furthermore, the effectiveness of the PLA’s autonomous systems is predicated on the quality of the data its sensors collect. This presents a prime opportunity to attack the information rather than the platform. As I’ve written about previously, sophisticated naval decoys could mimic the thermal and radar signatures of high-value U.S. assets, spoofing an entire PLA swarm into attacking empty ocean. Concerted electronic warfare can jam the specific datalink frequencies used by the drones to coordinate, causing the swarm to devolve from a coherent unit into a confused mob.
This brings into sharp relief the contrasting U.S. approach to autonomous warfare. Where the PLA’s “Mothership Warfare” concept uses unmanned systems primarily as an enabler for its long-range missile forces, the U.S. concept for Collaborative Combat Aircraft (CCAs) envisions them as direct extensions of its manned fighter force, designed to achieve air and sea control. The operational divergence is stark. The PLA’s drone is a key to unlock a door for a missile; the U.S. CCA is a weapon to kick the door down itself.
Here we’re presented with two fundamentally different philosophies, born from the distinct technical and engineering approaches I detailed in the first part of this series. On one hand, we have the PLA’s vertically integrated, hardware-centric architecture. It is optimized for specific missions, like the magazine depletion strike, but its proprietary nature may render it brittle and less adaptable. On the other, we have the U.S.’s software-defined, Modular Open Systems Approach (MOSA), which prioritizes network resilience and interoperability but may be slower to field and more complex to integrate.
So which of these competing philosophies is better suited to the harsh operational realities and immense geographical challenges of a high-intensity conflict in the Western Pacific? I’m not quite sure, but I do know the answer to this question—a question of both engineering design and operational art—will likely determine the future of air and sea power in the 21st century.







From the U.S. perspective, it seems critical to establish a monitoring system that can track not only AIS data from long-docked vessels, but also long-term container storage at major ports.
At the same time, disrupting the data links between Chinese drone swarms—effectively severing their communication—could degrade the swarm into isolated units, significantly reducing their operational effectiveness.
To avoid wasting high-end interceptors on low-value drone attacks, a point-based targeting framework that enables precise strikes against command nodes would also be essential.
In particular, when platforms like the J-20 operate in electronic silence, that very silence should be reframed as a signal of imminent threat. A passive sensor network fused with satellite intelligence could enable early detection of these otherwise invisible approaches.
In the end, a commander with broad situational awareness—who doesn't fixate on minor threats—will always remain one step ahead of the drones. Thank you for the insightful piece, truly appreciated.
Really appreciate your work.